OpenSSL is a toolkit and a cryptography library that support the Secure Sockets Layer (SSL)) and Transport Layer Security (TLS) protocol on Linux.
It provides cryptographic protocols to varies applications running on Linux such as ssh, Apache (httpd), Nginx, etc.
TLS is a cryptographic protocol used to secure network communications between the devices.
OpenSSL configuration file is located at /etc/pki/tls/openssl.cnf, referred to as the master configuration file, which is read by the OpenSSL library.
In this guide, we will show you how to check supported TLS and SSL ciphers (version) on opneSUSE system. The same procedure is applicable for other distribution as well.
How to check what SSL or TLS protocol versions are supported on a Linux system:
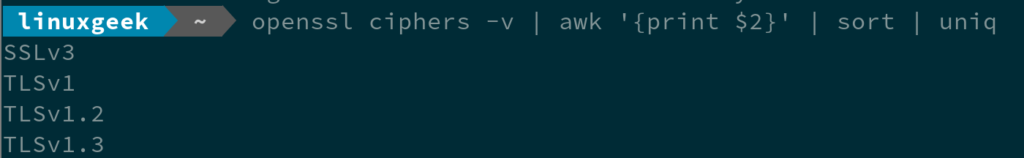
To check list of supported SSL or TLS protocol versions on a your Linux system, run:
You need to use a combination of sort and uniq commands to get the list, because the uniq command will only remove duplicate lines that are instantaneous to each other.
openssl ciphers -v | awk '{print $2}' | sort | uniq
SSLv3
TLSv1
TLSv1.2
TLSv1.3
To get a list of all cipher suites supported by your installation of OpenSSL, run:
openssl ciphers -v | column -t TLS_AES_256_GCM_SHA384 TLSv1.3 Kx=any Au=any Enc=AESGCM(256) Mac=AEAD TLS_CHACHA20_POLY1305_SHA256 TLSv1.3 Kx=any Au=any Enc=CHACHA20/POLY1305(256) Mac=AEAD TLS_AES_128_GCM_SHA256 TLSv1.3 Kx=any Au=any Enc=AESGCM(128) Mac=AEAD ECDHE-ECDSA-AES256-GCM-SHA384 TLSv1.2 Kx=ECDH Au=ECDSA Enc=AESGCM(256) Mac=AEAD ECDHE-RSA-AES256-GCM-SHA384 TLSv1.2 Kx=ECDH Au=RSA Enc=AESGCM(256) Mac=AEAD DHE-RSA-AES256-GCM-SHA384 TLSv1.2 Kx=DH Au=RSA Enc=AESGCM(256) Mac=AEAD ECDHE-ECDSA-CHACHA20-POLY1305 TLSv1.2 Kx=ECDH Au=ECDSA Enc=CHACHA20/POLY1305(256) Mac=AEAD ECDHE-RSA-CHACHA20-POLY1305 TLSv1.2 Kx=ECDH Au=RSA Enc=CHACHA20/POLY1305(256) Mac=AEAD DHE-RSA-CHACHA20-POLY1305 TLSv1.2 Kx=DH Au=RSA Enc=CHACHA20/POLY1305(256) Mac=AEAD ECDHE-ECDSA-AES128-GCM-SHA256 TLSv1.2 Kx=ECDH Au=ECDSA Enc=AESGCM(128) Mac=AEAD ECDHE-RSA-AES128-GCM-SHA256 TLSv1.2 Kx=ECDH Au=RSA Enc=AESGCM(128) Mac=AEAD DHE-RSA-AES128-GCM-SHA256 TLSv1.2 Kx=DH Au=RSA Enc=AESGCM(128) Mac=AEAD ECDHE-ECDSA-AES256-SHA384 TLSv1.2 Kx=ECDH Au=ECDSA Enc=AES(256) Mac=SHA384 ECDHE-RSA-AES256-SHA384 TLSv1.2 Kx=ECDH Au=RSA Enc=AES(256) Mac=SHA384 DHE-RSA-AES256-SHA256 TLSv1.2 Kx=DH Au=RSA Enc=AES(256) Mac=SHA256 ECDHE-ECDSA-AES128-SHA256 TLSv1.2 Kx=ECDH Au=ECDSA Enc=AES(128) Mac=SHA256 ECDHE-RSA-AES128-SHA256 TLSv1.2 Kx=ECDH Au=RSA Enc=AES(128) Mac=SHA256 DHE-RSA-AES128-SHA256 TLSv1.2 Kx=DH Au=RSA Enc=AES(128) Mac=SHA256 ECDHE-ECDSA-AES256-SHA TLSv1 Kx=ECDH Au=ECDSA Enc=AES(256) Mac=SHA1 ECDHE-RSA-AES256-SHA TLSv1 Kx=ECDH Au=RSA Enc=AES(256) Mac=SHA1 DHE-RSA-AES256-SHA SSLv3 Kx=DH Au=RSA Enc=AES(256) Mac=SHA1 ECDHE-ECDSA-AES128-SHA TLSv1 Kx=ECDH Au=ECDSA Enc=AES(128) Mac=SHA1 ECDHE-RSA-AES128-SHA TLSv1 Kx=ECDH Au=RSA Enc=AES(128) Mac=SHA1 DHE-RSA-AES128-SHA SSLv3 Kx=DH Au=RSA Enc=AES(128) Mac=SHA1 RSA-PSK-AES256-GCM-SHA384 TLSv1.2 Kx=RSAPSK Au=RSA Enc=AESGCM(256) Mac=AEAD DHE-PSK-AES256-GCM-SHA384 TLSv1.2 Kx=DHEPSK Au=PSK Enc=AESGCM(256) Mac=AEAD RSA-PSK-CHACHA20-POLY1305 TLSv1.2 Kx=RSAPSK Au=RSA Enc=CHACHA20/POLY1305(256) Mac=AEAD DHE-PSK-CHACHA20-POLY1305 TLSv1.2 Kx=DHEPSK Au=PSK Enc=CHACHA20/POLY1305(256) Mac=AEAD ECDHE-PSK-CHACHA20-POLY1305 TLSv1.2 Kx=ECDHEPSK Au=PSK Enc=CHACHA20/POLY1305(256) Mac=AEAD AES256-GCM-SHA384 TLSv1.2 Kx=RSA Au=RSA Enc=AESGCM(256) Mac=AEAD PSK-AES256-GCM-SHA384 TLSv1.2 Kx=PSK Au=PSK Enc=AESGCM(256) Mac=AEAD PSK-CHACHA20-POLY1305 TLSv1.2 Kx=PSK Au=PSK Enc=CHACHA20/POLY1305(256) Mac=AEAD RSA-PSK-AES128-GCM-SHA256 TLSv1.2 Kx=RSAPSK Au=RSA Enc=AESGCM(128) Mac=AEAD DHE-PSK-AES128-GCM-SHA256 TLSv1.2 Kx=DHEPSK Au=PSK Enc=AESGCM(128) Mac=AEAD AES128-GCM-SHA256 TLSv1.2 Kx=RSA Au=RSA Enc=AESGCM(128) Mac=AEAD PSK-AES128-GCM-SHA256 TLSv1.2 Kx=PSK Au=PSK Enc=AESGCM(128) Mac=AEAD AES256-SHA256 TLSv1.2 Kx=RSA Au=RSA Enc=AES(256) Mac=SHA256 AES128-SHA256 TLSv1.2 Kx=RSA Au=RSA Enc=AES(128) Mac=SHA256 ECDHE-PSK-AES256-CBC-SHA384 TLSv1 Kx=ECDHEPSK Au=PSK Enc=AES(256) Mac=SHA384 ECDHE-PSK-AES256-CBC-SHA TLSv1 Kx=ECDHEPSK Au=PSK Enc=AES(256) Mac=SHA1 SRP-RSA-AES-256-CBC-SHA SSLv3 Kx=SRP Au=RSA Enc=AES(256) Mac=SHA1 SRP-AES-256-CBC-SHA SSLv3 Kx=SRP Au=SRP Enc=AES(256) Mac=SHA1 RSA-PSK-AES256-CBC-SHA384 TLSv1 Kx=RSAPSK Au=RSA Enc=AES(256) Mac=SHA384 DHE-PSK-AES256-CBC-SHA384 TLSv1 Kx=DHEPSK Au=PSK Enc=AES(256) Mac=SHA384 RSA-PSK-AES256-CBC-SHA SSLv3 Kx=RSAPSK Au=RSA Enc=AES(256) Mac=SHA1 DHE-PSK-AES256-CBC-SHA SSLv3 Kx=DHEPSK Au=PSK Enc=AES(256) Mac=SHA1 AES256-SHA SSLv3 Kx=RSA Au=RSA Enc=AES(256) Mac=SHA1 PSK-AES256-CBC-SHA384 TLSv1 Kx=PSK Au=PSK Enc=AES(256) Mac=SHA384 PSK-AES256-CBC-SHA SSLv3 Kx=PSK Au=PSK Enc=AES(256) Mac=SHA1 ECDHE-PSK-AES128-CBC-SHA256 TLSv1 Kx=ECDHEPSK Au=PSK Enc=AES(128) Mac=SHA256 ECDHE-PSK-AES128-CBC-SHA TLSv1 Kx=ECDHEPSK Au=PSK Enc=AES(128) Mac=SHA1 SRP-RSA-AES-128-CBC-SHA SSLv3 Kx=SRP Au=RSA Enc=AES(128) Mac=SHA1 SRP-AES-128-CBC-SHA SSLv3 Kx=SRP Au=SRP Enc=AES(128) Mac=SHA1 RSA-PSK-AES128-CBC-SHA256 TLSv1 Kx=RSAPSK Au=RSA Enc=AES(128) Mac=SHA256 DHE-PSK-AES128-CBC-SHA256 TLSv1 Kx=DHEPSK Au=PSK Enc=AES(128) Mac=SHA256 RSA-PSK-AES128-CBC-SHA SSLv3 Kx=RSAPSK Au=RSA Enc=AES(128) Mac=SHA1 DHE-PSK-AES128-CBC-SHA SSLv3 Kx=DHEPSK Au=PSK Enc=AES(128) Mac=SHA1 AES128-SHA SSLv3 Kx=RSA Au=RSA Enc=AES(128) Mac=SHA1 PSK-AES128-CBC-SHA256 TLSv1 Kx=PSK Au=PSK Enc=AES(128) Mac=SHA256 PSK-AES128-CBC-SHA SSLv3 Kx=PSK Au=PSK Enc=AES(128) Mac=SHA1
1) Verify SSL & TLS version support with nmap command
nmap (Network Mapper) is a powerful open source network scanning tool that is used to scan for open ports and associated services on a network.
Also, you can use the nmap command to check supported SSL and TLS version on the remote web server.
nmap --script +ssl-enum-ciphers -p 443 www.2daygeek.com Starting Nmap 7.70 ( https://nmap.org ) at 2021-11-25 20:56 IST Nmap scan report for www.2daygeek.com (104.21.80.108) Host is up (0.0045s latency). Other addresses for www.2daygeek.com (not scanned): 172.67.179.102 2606:4700:3033::6815:506c 2606:4700:3035::ac43:b366 PORT STATE SERVICE 443/tcp open https | ssl-enum-ciphers: | TLSv1.0: | ciphers: | TLS_ECDHE_ECDSA_WITH_AES_128_CBC_SHA (ecdh_x25519) - A | TLS_ECDHE_ECDSA_WITH_AES_256_CBC_SHA (ecdh_x25519) - A | compressors: | NULL | cipher preference: server | TLSv1.1: | ciphers: | TLS_ECDHE_ECDSA_WITH_AES_128_CBC_SHA (ecdh_x25519) - A | TLS_ECDHE_ECDSA_WITH_AES_256_CBC_SHA (ecdh_x25519) - A | compressors: | NULL | cipher preference: server | TLSv1.2: | ciphers: | TLS_ECDHE_ECDSA_WITH_AES_128_CBC_SHA (ecdh_x25519) - A | TLS_ECDHE_ECDSA_WITH_AES_128_CBC_SHA256 (ecdh_x25519) - A | TLS_ECDHE_ECDSA_WITH_AES_128_GCM_SHA256 (ecdh_x25519) - A | TLS_ECDHE_ECDSA_WITH_AES_256_CBC_SHA (ecdh_x25519) - A | TLS_ECDHE_ECDSA_WITH_AES_256_CBC_SHA384 (ecdh_x25519) - A | TLS_ECDHE_ECDSA_WITH_AES_256_GCM_SHA384 (ecdh_x25519) - A | TLS_ECDHE_ECDSA_WITH_CHACHA20_POLY1305_SHA256 (ecdh_x25519) - A | TLS_ECDHE_ECDSA_WITH_CHACHA20_POLY1305_SHA256-draft (ecdh_x25519) - A | compressors: | NULL | cipher preference: client |_ least strength: A Nmap done: 1 IP address (1 host up) scanned in 13.81 seconds
The above output will show detailed information, but if you only want to check the supported TLS version, run the following command.
nmap --script +ssl-enum-ciphers -p 443 www.2daygeek.com | egrep "SSLv|TLSv"
| TLSv1.0:
| TLSv1.1:
| TLSv1.2:
To check the supported/enabled TLS version on multiple ports simultaneously, run the below command.
for port in 443 9090; do echo $prot:; nmap --script +ssl-enum-ciphers -p $port localhost | grep -e TLSv -e SSLv; done
443:
| TLSv1.0:
| TLSv1.1:
| TLSv1.2:
9090:
| TLSv1.2:
2) How to check supported SSL and TLS version using openssl command
You can’t check the list of supported SSL and TLS versions in one go using an openssl command such as nmap command, but instead check whether a specific SSL or TLS version is supported by the remote web server as shown below:
If you receive the certificate chain and the SSL handshake verification is ok, the given TLS protocol will be supported.
openssl s_client -connect www.2daygeek.com:443 -tls1_2
CONNECTED(00000003)
depth=2 C = IE, O = Baltimore, OU = CyberTrust, CN = Baltimore CyberTrust Root
verify return:1
depth=1 C = US, O = "Cloudflare, Inc.", CN = Cloudflare Inc ECC CA-3
verify return:1
depth=0 C = US, ST = California, L = San Francisco, O = "Cloudflare, Inc.", CN = sni.cloudflaressl.com
verify return:1
---
Certificate chain
0 s:C = US, ST = California, L = San Francisco, O = "Cloudflare, Inc.", CN = sni.cloudflaressl.com
i:C = US, O = "Cloudflare, Inc.", CN = Cloudflare Inc ECC CA-3
1 s:C = US, O = "Cloudflare, Inc.", CN = Cloudflare Inc ECC CA-3
i:C = IE, O = Baltimore, OU = CyberTrust, CN = Baltimore CyberTrust Root
---
Server certificate
-----BEGIN CERTIFICATE-----
MIIFNjCCBN2gAwIBAgIQCHdYtMg6xYFr1CCbVh9Z7jAKBggqhkjOPQQDAjBKMQsw
CQYDVQQGEwJVUzEZMBcGA1UEChMQQ2xvdWRmbGFyZSwgSW5jLjEgMB4GA1UEAxMX
Q2xvdWRmbGFyZSBJbmMgRUNDIENBLTMwHhcNMjEwNjEyMDAwMDAwWhcNMjIwNjEx
MjM1OTU5WjB1MQswCQYDVQQGEwJVUzETMBEGA1UECBMKQ2FsaWZvcm5pYTEWMBQG
A1UEBxMNU2FuIEZyYW5jaXNjbzEZMBcGA1UEChMQQ2xvdWRmbGFyZSwgSW5jLjEe
MBwGA1UEAxMVc25pLmNsb3VkZmxhcmVzc2wuY29tMFkwEwYHKoZIzj0CAQYIKoZI
zj0DAQcDQgAERStL2weesrGoc07u8L6KCPYeuW4pqBq3xHVfffNMRE6AwI/dItmv
tgkmSEtoqVIovcr1R8+gR60+5IEbfo6E3qOCA3gwggN0MB8GA1UdIwQYMBaAFKXO
N+rrsHUOlGeItEX62SQQh5YfMB0GA1UdDgQWBBQtKgMJzPHadN9LHJd+lCdc9tBb
XjA+BgNVHREENzA1gg4qLjJkYXlnZWVrLmNvbYIMMmRheWdlZWsuY29tghVzbmku
Y2xvdWRmbGFyZXNzbC5jb20wDgYDVR0PAQH/BAQDAgeAMB0GA1UdJQQWMBQGCCsG
AQUFBwMBBggrBgEFBQcDAjB7BgNVHR8EdDByMDegNaAzhjFodHRwOi8vY3JsMy5k
aWdpY2VydC5jb20vQ2xvdWRmbGFyZUluY0VDQ0NBLTMuY3JsMDegNaAzhjFodHRw
Oi8vY3JsNC5kaWdpY2VydC5jb20vQ2xvdWRmbGFyZUluY0VDQ0NBLTMuY3JsMD4G
A1UdIAQ3MDUwMwYGZ4EMAQICMCkwJwYIKwYBBQUHAgEWG2h0dHA6Ly93d3cuZGln
aWNlcnQuY29tL0NQUzB2BggrBgEFBQcBAQRqMGgwJAYIKwYBBQUHMAGGGGh0dHA6
Ly9vY3NwLmRpZ2ljZXJ0LmNvbTBABggrBgEFBQcwAoY0aHR0cDovL2NhY2VydHMu
ZGlnaWNlcnQuY29tL0Nsb3VkZmxhcmVJbmNFQ0NDQS0zLmNydDAMBgNVHRMBAf8E
AjAAMIIBfgYKKwYBBAHWeQIEAgSCAW4EggFqAWgAdQApeb7wnjk5IfBWc59jpXfl
vld9nGAK+PlNXSZcJV3HhAAAAXn9je5zAAAEAwBGMEQCIBT9ZzRRii0yPm9LwAzj
lOAjSAOfws3MY+CQuOWqLtWOAiAG/56GezshwutHzqKGYUob/FG+v1kdDy+Fdv8C
5EDl4QB2ACJFRQdZVSRWlj+hL/H3bYbgIyZjrcBLf13Gg1xu4g8CAAABef2N7roA
AAQDAEcwRQIhAIRFfUcMG39Xm/kM0hhz7w9ZpH65Sekmc6HB6+Py0M2TAiBoGC2p
0FIRyu+15Ea3qLfhrJhyvR0vdFlyUma0QNXq6gB3AFGjsPX9AXmcVm24N3iPDKR6
zBsny/eeiEKaDf7UiwXlAAABef2N7t8AAAQDAEgwRgIhAIADK/cNu/97AJNUvb7b
yhbbxsshzo4vZQASEoLhwTyEAiEAtrmHdMWeziuIn+sKRJs+DMEU2saI7NxBQ/3b
bnBzH0cwCgYIKoZIzj0EAwIDRwAwRAIgK8+jVc3v78/zYQCUFmdW4CuikrO6tN3H
FUJpxnTP/wICIAKDRDUZz+Mk7NXolsF2LoXsWqwsuZjaf/DBog2/EBib
-----END CERTIFICATE-----
subject=C = US, ST = California, L = San Francisco, O = "Cloudflare, Inc.", CN = sni.cloudflaressl.com
issuer=C = US, O = "Cloudflare, Inc.", CN = Cloudflare Inc ECC CA-3
---
No client certificate CA names sent
Peer signing digest: SHA256
Peer signature type: ECDSA
Server Temp Key: X25519, 253 bits
---
SSL handshake has read 2784 bytes and written 304 bytes
Verification: OK
---
New, TLSv1.2, Cipher is ECDHE-ECDSA-CHACHA20-POLY1305
Server public key is 256 bit
Secure Renegotiation IS supported
Compression: NONE
Expansion: NONE
No ALPN negotiated
SSL-Session:
Protocol : TLSv1.2
Cipher : ECDHE-ECDSA-CHACHA20-POLY1305
Session-ID: 1E17DBCE53C0F14C2F66C6BFEB200FF5116F1F15AAAA75AB1F8BA68A8646BDBA
Session-ID-ctx:
Master-Key: A3A18C7F602296882D41FC0684BEB195B65B10D82769C7C92ED3070C895C9CEC6B3890F751D1B43824244123FC438ACA
PSK identity: None
PSK identity hint: None
SRP username: None
TLS session ticket lifetime hint: 64800 (seconds)
TLS session ticket:
0000 - 90 d4 e4 e4 dc 6f d2 53-d6 f0 2d c9 b5 c3 1a 29 .....o.S..-....)
0010 - 29 9c f5 19 26 fc 44 02-9c 60 c3 14 98 f3 95 c3 )...&.D..`......
0020 - 2b c5 d6 49 fa 79 98 ae-30 90 5a c2 aa 74 69 20 +..I.y..0.Z..ti
0030 - fa 73 a6 8c 3f fc e3 d5-80 49 b1 de ec b5 fc 27 .s..?....I.....'
0040 - 7e b8 8b da ab 88 3a 90-97 ce fa 81 25 80 87 29 ~.....:.....%..)
0050 - 44 80 53 e9 a5 69 bd fe-77 0d d6 af 71 7e 7c f8 D.S..i..w...q~|.
0060 - be 1f 95 7d d8 7e e8 11-c3 ca 2c 86 b4 c0 16 6b ...}.~....,....k
0070 - 75 d3 56 05 2f e2 e7 38-a8 d1 23 80 87 94 6c f3 u.V./..8..#...l.
0080 - c4 32 80 55 6d 75 07 de-a3 15 c9 15 c9 13 76 ad .2.Umu........v.
0090 - 8d 4f ab d8 6f 71 78 be-32 05 94 5a c1 29 13 ad .O..oqx.2..Z.)..
00a0 - c1 da c4 64 dd 9a ba 53-b3 97 4d 1f f7 1f 39 a9 ...d...S..M...9.
00b0 - b2 03 d5 97 58 e8 5d ef-51 6d 9f ae 41 aa a7 51 ....X.].Qm..A..Q
Start Time: 1637854673
Timeout : 7200 (sec)
Verify return code: 0 (ok)
Extended master secret: yes
---
closed
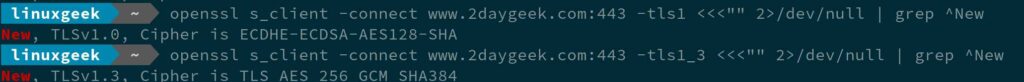
To check other SSL and TLS protocol using openssl, run:
For TLS 1.3, run:
openssl s_client -connect www.2daygeek.com:443 -tls1_3 <<<"" 2>/dev/null | grep ^New
For TLS 1.0, run:
openssl s_client -connect www.2daygeek.com:443 -tls1 <<<"" 2>/dev/null | grep ^New
Closing Notes
In this guide, we’ve shown you how to check supported TLS and SSL version and ciphers in Linux system or website using openssl and nmap command.
This procedure was tested on openSUSE system, but the same procedure would work other Linux systems too.
If you have any questions or feedback, feel free to comment below.



